Today’s optical networks are like superhighways for information, using light to send large amounts of data quickly over long distances. While this has allowed for some exciting emerging applications, it also offers cyber criminals a higher degree of temptation, thanks to the bigger data “prize.”
One of the key vulnerabilities of optical networks lies in their physical infrastructure. The fibre-optic cables that carry the data do so in diverse environments, including underground installations, undersea cables, and utility conduits. This exposure can make them susceptible to physical tampering, such as tapping into the fibre-optic cables, which can result in data interception and breaches.
Even the biggest brands are not immune to cyber security threats. In 2021 LinkedIn was hacked in an attack that saw data from around 700 million users posted on a dark web forum. More recently, social media site Reddit had some 80GB of data stolen by a ransomware gang, which threatened to sell it if the company did not pay $4.5m to delete it.
Optical networks are no less vulnerable. The convergence of fibre-optic networks with IP-based systems can expose them to a wide range of cyber attacks, including distributed denial of service (DDoS), data interception, and unauthorised access. The potential consequences of a security breach in an optical network extend beyond data loss, encompassing service disruption, damage to a company's reputation and then the financial impact.
Paul Momtahan, Director of Solutions at Infinera explains: “According to the latest IBM report [1], the global average cost of a data breach is $4.45m, and in the US, it's almost 10 million. There's also legislation and the risk of big fines, for example, there is the GDPR in Europe, and that can be up to €20m or 4% of your turnover, whichever is higher. And then in California, you've got the California Consumer Privacy Act. And that can be between $100-150 per California resident, and there are 40 million residents in California. So a data breach can be very expensive.”
Operators of fibre networks have an advantage in that fibre is known to be more secure and more difficult to penetrate than other network technology because the way that it transmits data makes the signal trickier to intercept. But even fibre is not impenetrable to cyber criminals. Operators need the best strategies to protect their network data, both while “at rest” at the data centre or storage facility and, crucially, in the optical layer when it is in transit in the fibre itself.
The advantages of encryption
Encryption at the optical layer and optical steganography for data-hiding are both ways to offer a high level of protection. Encryption works by converting data into an unreadable format using cryptographic algorithms.
In terms of the benefits to operators, encryption guarantees that only authorised parties can access and understand the transmitted data, while safeguarding its integrity by ensuring that it remains unaltered during transmission. Any unauthorised modifications to the encrypted data will alert operators to potential tampering. Encryption can also be paired with authentication mechanisms to ensure that both the sender and receiver of data are genuine. Encryption enables secure remote access to optical networks, allowing authorised personnel to manage and monitor the network from anywhere without compromising its security.
Layer 1 encryption in particular is useful for protecting the data at the physical layer, for performance critical applications such as networks. This method ensures that there is no overhead data and that encryption can be carried out at line speed with 100% data throughput. Since the data is encrypted directly at the optical level, it is protected even before it enters higher network layers, making it more difficult for attackers to intercept or tamper with the data.
Layer 1 encryption also has the advantage of offering better network performance, as encryption and decryption will be handled by specialised hardware at the physical layer. This can minimise the impact on network latency and throughput. Layer 1 encryption can also be simpler to manage and configure since it is applied to the entire optical link without the need for complex routing configurations. This method also offers scalability benefits for large networks with high traffic volumes.
Momtahan says: “There are a few benefits of encrypting at layer 1, one is that you get very high throughput at low cost. It's much more complication-intensive to do it at, say layer three with IPsec. You also get lower latency, you don't waste a lot of protocol overhead, which you get with IPsec – there's no protocol overhead for the layer one encryption. It’s also multi-protocol. So, it can do, say, your fibre channel or non IP protocols, in addition to your regular IP and Ethernet.”
Leveraging layer 1 encryption for network operators
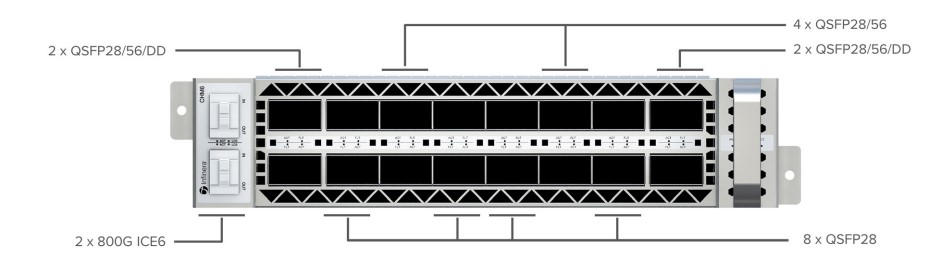
Recognising these benefits to network operator customers, Infinera offers layer 1 encryption for enhanced security, available on CHM6 Xponder sleds for the GX G42 compact modular platform. Managed through the Transcend Network Management System (TNMS), this encryption option ensures secure data centre interconnect (DCI) with encrypted wavelengths between data centres. It can also support encryption for enterprise and wholesale customers, securing internal traffic across vulnerable environments.
The company’s solution enables wirespeed bulk encryption, protecting data over the entire concatenated optical data unit, including Ethernet (100 GbE, 400 GbE), and OTU4 client traffic. The encryption is symmetric, employing the same encryption key for both ends, ensuring high throughput and low latency.
The encryption is authenticated and authorised using Internet Key Exchange version 2 (IKEv2). X.509 certificates or pre-shared keys (PSKs) can be used for secure key exchange.
Elliptic curve Diffie-Hellman ephemeral (ECDHE) ensures a shared data encryption key without revealing secret data. The data plane encryption employs AES-256-GCM, offering strong protection and integrity. Says Momtahan: “One of the keys to good security is how the key itself is exchanged and how to do the authentication authorisation that sits above that. The key needs to be kept secret so we use the ECDHE algorithm, which is a standard protocol for creating the same key at both ends without sharing or transmitting any secret data.”
Infinera’s solution also uses key rotation, as Momtahan continues: “We rotate the key that we're using in the in the in the DSP every one minute to 60 minutes, which makes it harder for somebody to, to potentially crack that key because there’s only a limited amount of data they could store to analyse. If they did manage to crack it, they would only be able to decrypt minutes worth of information, and couldn’t go back in time and decrypt previously stored messages.”
The CHM6 encryption solution is designed to meet rigorous security standards. It aligns with FIPS 140-3 Level 2 and is planned for NIAP Common Criteria Network Device Collaborative Protection Profile certification. Inclusion on the U.S. Department of Defense's Joint Interoperability Test Command (JITC) Approved Products List (APL) is also targeted. The Layer 1 encryption on the CHM6 sled for the GX G42 is also designed to offer robust security for data centre interconnects (DCI) and other applications. With high-speed encryption, secure key exchange, and compliance with industry standards, it can provide operators with a comprehensive solution to safeguard data in transit.